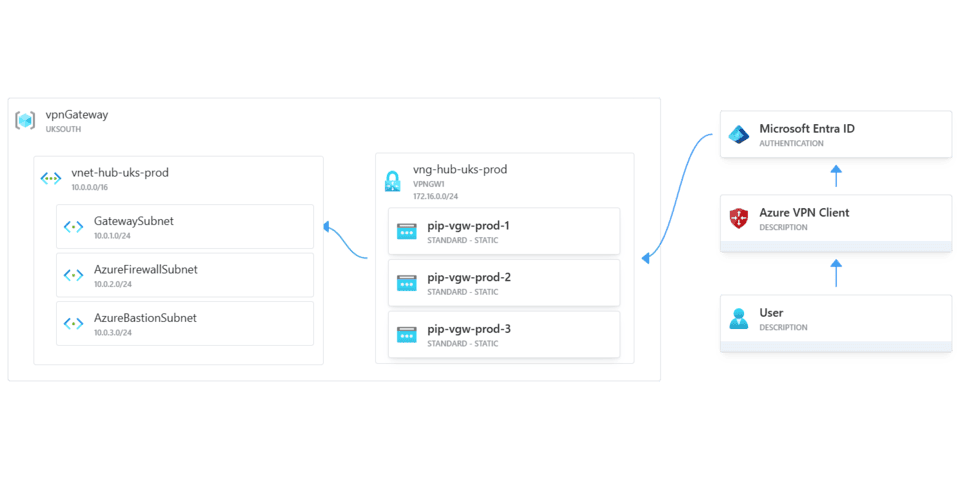
Azure VPN Gateway & Hub Vnet deployed via IaC
- Components of the Bicep files
- Deployments
- Azure VPN Configuration
- Connecting after deployment of the VPN gateway
- Improvements
Components of the Bicep files
The repo contains 2 bicep files, the primary main.bicep file is used to pass through parameters to the 2 modules:
-
module-hubVnet.bicep
Creates a hub Vnet with 3 subnets, GatewaySubnet, AzureBastionSubnet & AzureFirewallSubnet -
module-virtualNetworkGateway.bicep
Deploys an active-active VPN gateway into the Gateway subnet within the hubVnet
The VPN Gateway requires 3 PIPs for this configuration
The VPN Gateway is set to assign devices an IP in the 172.16.0.0/24 block dynamically
The VPN Gateway is configured to support authentication via Entra, this is facilitated through the Azure VPN enterprise app
Prior to deployment make sure to authorise the Azure VPN app for your tenant
Deployment
First download the files from the repo
You will need to enter your Entra tenantId for the virtualNetworkGateway module, specifically the paramAadTenantId parameter
You may also want to customise the tags/other values but the tenantID is the only hard requirement
Deployment takes about 20mins since the VPN Gateway configures other hidden resources
Azure VPN Configuration
While waiting for the deployment to complete you can also restrict access to the Azure VPN app to make sure only a certain users can auth against it an in turn connect to the VPN
Assuming you have authorised the Azure VPN app it will be available under ‘Enterprise Apps’
To restrict access to a certain set of users/group under the apps ‘Properties’ set ‘Assignment Required?’ to ‘Yes’
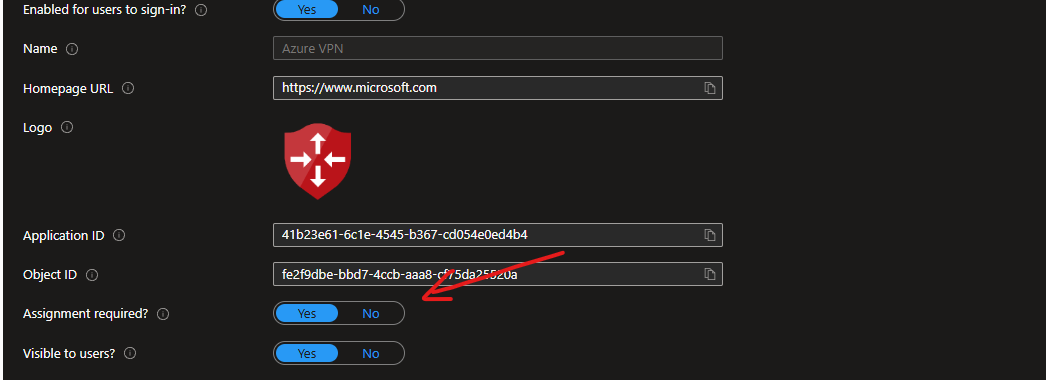
After this you can then just add individual users/groups under the ‘Users and Groups’ tab
If you also have the appropriate EntraID licensing you can also use a conditional access policy scoped to the Azure VPN app for additional restrictions such as:
- Requiring MFA
- Requiring an Entra-managed device
- Blocking login attempts from specific locations
Since I am GA in my tenant MFA is required by default but for regular users you would want a CA policy to further restrict access to the app, and following Zero Trust principles you would want them to MFA for every connection to the VPN as well as restricting the devices they can connect from to reduce the risk of leaked config/credentials being able to connect to the VPN
Connecting after deployment of the VPN gateway
First download the Azure VPN Client app manually or deploy it through your MDM
Then go to your VPN Gateway resource in Azure and under ‘Settings’ > ‘Point-to-site-configuration’ > ‘Download VPN client’
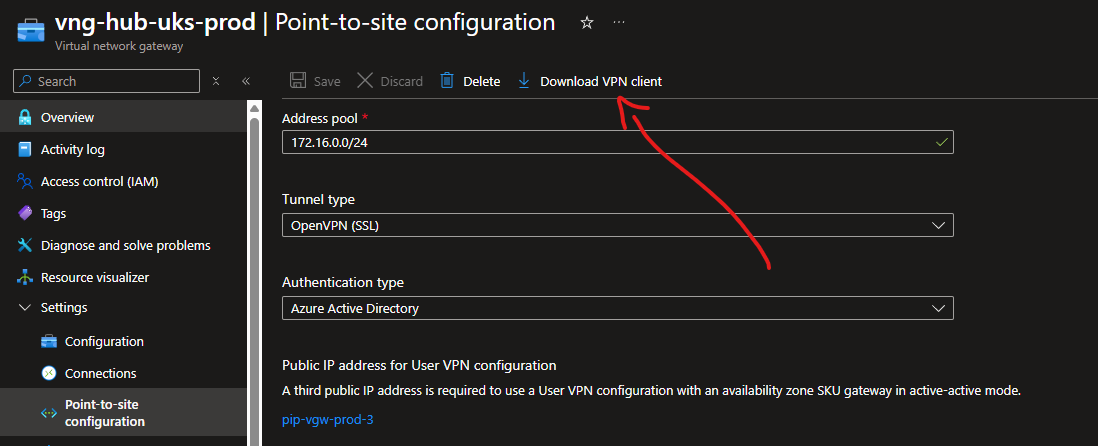
This will download a .zip package with the config you need to import into the Azure VPN Client app
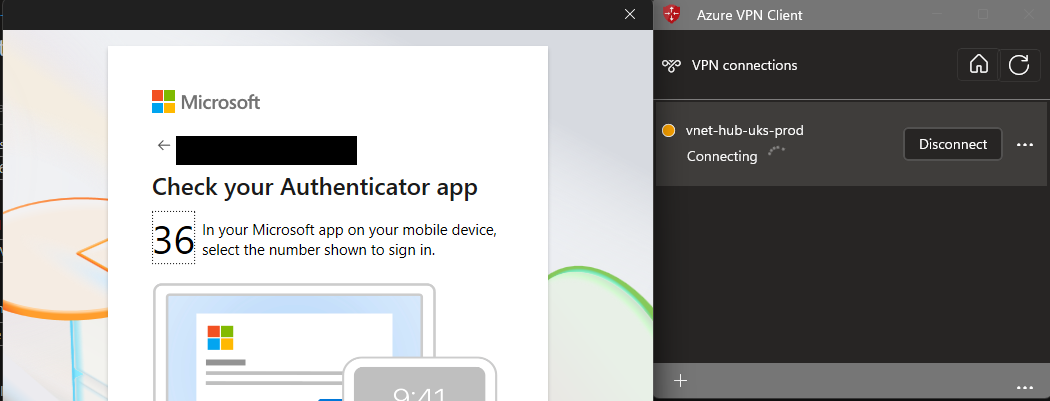
Once you import the config you are then able to connect to the to the VPN
The app will SSO with other office apps so assuming you have already signed into another app it will bypass the need for MFA (unless otherwise required by a CA policy)
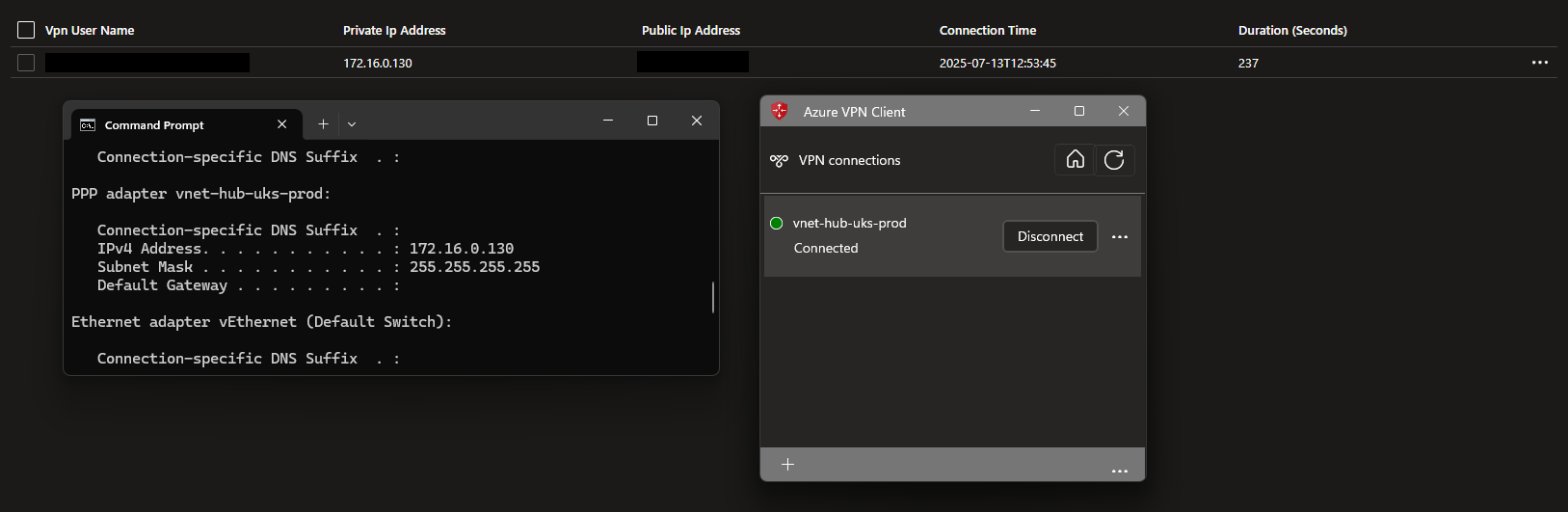
Once connected you can check the VPN Gateway resource to see active connections found under ‘Monitoring’ > ‘Point-to-site Sessions’
Note this page only updates every 5mins so your client may not appear straight away
Improvements
If this setup is to be used in a prod environment you would also want to use a VPN Gateway SKU that supports AZs to distribute the gateway across another AZ (e.g. VpnGw1AZ)
This requires you switch the VPN Gateway generation to ‘Generation 2’, this supports AZs for redundancy and HA but also offers higher throughput
Migration between Generation 1 & Gen 2 VPN Gateways is not possible so if you want to upgrade/downgrade you would have to delete and reprovision the gateway